Introduction to O DATA Security
O DATA security is a critical aspect of building and deploying O DATA services. As O DATA enables seamless data exchange between clients and servers, it becomes essential to protect sensitive data, prevent unauthorized access, and ensure data integrity. In this article, we will explore the key elements of O DATA security, focusing on authentication and authorization mechanisms, securing O DATA endpoints, and the integration of OAuth with O DATA for enhanced security.
Authentication and Authorization Mechanisms
Authentication is the process of verifying the identity of a user or client attempting to access an O DATA service. Proper authentication mechanisms ensure that only authorized users can interact with the data and perform CRUD operations. There are various authentication methods that O DATA services can employ:
-
-
- Basic Authentication: Basic authentication involves sending the username and password in the request headers. However, this method is not recommended for production environments as it transmits credentials in plain text, which poses security risks.
-
- Token-Based Authentication: Token-based authentication is a more secure approach. Clients obtain an access token after successful login, which they include in subsequent requests to authenticate themselves. This way, sensitive credentials are not exposed in every request.
-
- OAuth Authentication: OAuth is an industry-standard protocol used for delegated authorization and secure authentication. It allows users to grant limited access to their resources without sharing their credentials directly. OAuth is widely adopted for secure user authentication in O DATA services.
Authorization in O DATA
Authorization determines the level of access and actions a user can perform within an O DATA service after successful authentication. It ensures that authenticated users have appropriate permissions to access specific resources and perform CRUD operations. O DATA services use authorization mechanisms to enforce access control and protect sensitive data from unauthorized users.
Securing O DATA Endpoints
Configuring Secure HTTPS Connections
Securing O DATA endpoints with HTTPS (Hypertext Transfer Protocol Secure) is a fundamental step in O DATA security. HTTPS encrypts the data transmitted between clients and the server, preventing eavesdropping and data interception by malicious entities. It is crucial to configure the O DATA service to only accept HTTPS connections to ensure the privacy and integrity of the data exchanged.
Enabling CORS (Cross-Origin Resource Sharing)
CORS is a security feature implemented in web browsers to control cross-origin HTTP requests. By enabling CORS on the O DATA service, it becomes possible to specify which domains are allowed to access the service’s resources. This prevents unauthorized domains from making requests to the O DATA service, protecting it from cross-origin attacks.
OAuth and O DATA
Understanding OAuth
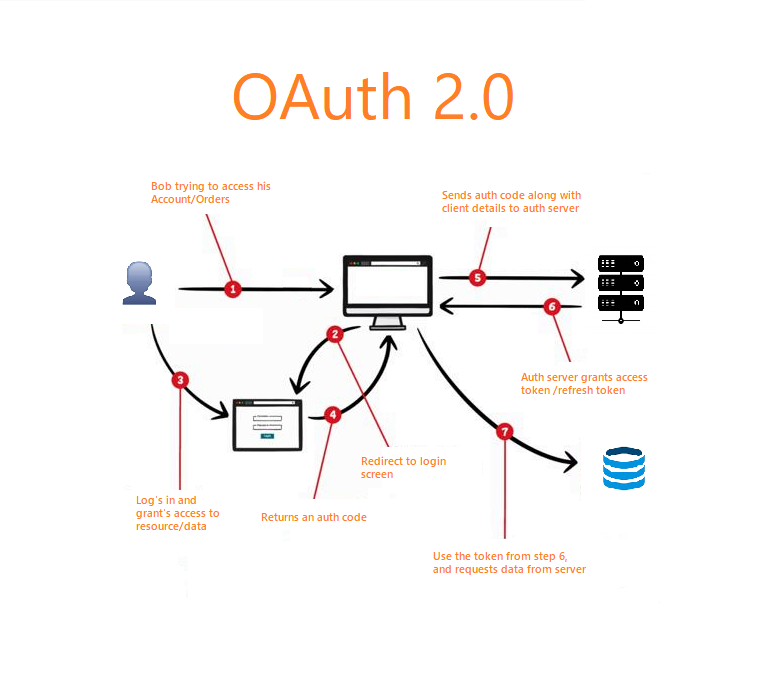
OAuth is an open standard protocol designed for secure authorization and access delegation. It allows third-party applications to access resources on behalf of a user without exposing the user’s credentials directly. OAuth provides a secure framework for delegating access to resources, making it a preferred choice for authentication in O DATA services.
Integration of OAuth with O DATA
Integrating OAuth with O DATA enhances security by implementing a robust authentication and authorization mechanism. When OAuth is employed in an O DATA service, clients request authorization from the OAuth provider, and upon successful authentication, they receive an access token. This token is then used to make authorized requests to the O DATA service, ensuring that only authenticated and authorized clients can access the data.
Conclusion
O DATA security is paramount to safeguarding data and ensuring a secure data exchange between clients and O DATA services. By implementing proper authentication and authorization mechanisms, securing O DATA endpoints with HTTPS, and integrating OAuth for enhanced security, developers can build robust and secure O DATA services. Emphasizing O DATA security allows organizations to protect sensitive information, maintain data integrity, and gain the trust of their users.
FAQs (Frequently Asked Questions)
-
-
- Is OAuth mandatory for securing O DATA services? OAuth is not mandatory but highly recommended for secure authentication and authorization in O DATA services. Other authentication methods can also be used based on specific use cases and security requirements.
-
- Can I use OAuth with any O DATA provider? Most modern O DATA providers support OAuth integration. However, it’s essential to verify the provider’s documentation to ensure compatibility.
-
- What are the benefits of using token-based authentication in O DATA? Token-based authentication enhances security by reducing the risk of credential exposure and simplifying the authentication process for clients.
-
- How does CORS protect O DATA services from cross-origin attacks? CORS allows servers to specify which domains can access their resources, preventing unauthorized domains from making cross-origin requests and protecting against cross-origin attacks.
-
- Can I use OAuth for both user authentication and authorization in O DATA? Yes, OAuth serves both authentication and authorization purposes in O DATA services. It allows clients to authenticate users and obtain access tokens for authorized data access.
Bonus: SAP ABAP – From Basic to Advanced OData
PART-4
PART-6
Find Your Preferred Courses
SAP SD (Sales and Distribution) is a module in the SAP ERP (Enterprise Resource Planning) system that handles all aspects of sales and distribution processes. S4 HANA is the latest version of SAP’s ERP suite, built on the SAP HANA in-memory database platform. It provides real-time data processing capabilities, improved…
SAP Human Capital Management (SAP HCM) is an important module in SAP. It is also known as SAP Human Resource Management System (SAP HRMS) or SAP Human Resource (HR). SAP HR software allows you to automate record-keeping processes. It is an ideal framework for the HR department to take advantage…
I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Salesforce Developer Training Overview Salesforce Developer training advances your skills and knowledge in building custom applications on the Salesforce platform using the programming capabilities of Apex code and the Visualforce UI framework. It covers all the fundamentals of application development through real-time projects and utilizes cases to help you clear…
SAP EWM stands for Extended Warehouse Management. It is a best-of-breed WMS Warehouse Management System product offered by SAP. It was first released in 2007 as a part of SAP SCM meaning Supply Chain Management suite, but in subsequent releases, it was offered as a stand-alone product. The latest version…
Oracle PL-SQL is actually the number one database. The demand in market is growing equally with the value of the database. It has become necessary for the Oracle PL-SQL certification to get the right job. eLearning Solutions is one of the renowned institutes for Oracle PL-SQL in Pune. We believe…
Course details for Pega Training in Pune Elearning solution is the best PEGA training institute in Pune. PEGA is one of the Business Process Management tool (BPM), its development is based on Java and OOP concepts. The PAGA technology is mainly used to improve business purposes and cost reduction. PEGA…
SAP PP Training Institute in Pune SAP PP training (Production Planning) is one of the largest functional modules in SAP. This module mainly deals with the production process like capacity planning, Master production scheduling, Material requirement planning shop floor, etc. The PP module of SAP takes care of the Master…
SAP BASIS Module Course Content (1) Hardware and Software Introduction (i) Hardware (a) Hardware Introduction (b) Architecture of different Hardware devices (ii) Software (a) Software Introduction (b) Languages and Software Development (c) Introduction to OS (d) Types of OS (iii) Database Concepts (a) Introduction (b) Database Architecture and concepts (c)…
Curriculum Details SAP HANA Administration SAP HANA Introduction SAP HANA Introduction SAP HANA Information Sources Installation Preparation SAP HANA Sizing Linux Operating system requirements SAP HANA Installation Introduction to SAP HANA Lifecycle Management tools Describing Advanced Installation options Explaining a Distributed system SAP HANA Architecture SAP HANA Architecture and Technology…
Business Warehouse (BW) is SAP’s data warehousing application; it uses an SAP NetWeaver application server, but can run on many different databases. Improvements come with each version of Courses for sap BW on HANA training, but a really big jump in functionality comes when SAP BW is installed on the…
SAP SAP HANA simple logistics is also known as HANA enterprise management. Different area of business is combined in this suit itself like HANA enterprise-management helps in faster and efficient processing of business data in the area of logistics, supply chain, procurement, user experience, sales, partner management. So Course for…
ABAP remains a key language as many SAP business applications and custom developments are written in ABAP, with Courses for sap ABAP on HANA training there are numerous improvements. The ABAP language, which allows writing streamlined ABAP code and benefit from SAP HANA. SAP HANA is a relational DBMS in SAP…
SAP HANA is the latest ERP Solution from SAP, which is a combination of Hardware and Software. HANA has unprecedented adoption by the SAP customers. courses for SAP HANA training institutes. SAP HANA is the latest, in-memory database, and platform which can be deployed on-premises or cloud. SAP HANA is a…
Oracle Applications R12 HRMS is one of the most demanded applications by most organizations. It is the core application possess by the ERP system. The core objective of the organization to implement Oracle R12 HRMS is to organize the entire activates of human resources management. An Elearning solution is well…
Elearning solutions provide training suit for Oracle Apps R12 SCM with training from industry experts. The organizations are adopting Oracle’s supply chain management cloud as they deliver the insights, visibility, and capabilities for organizations’ management. Oracle Apps R12 SCM allows the industry to create own intelligent supply chain. Hence, it…
Oracle Apps R12 Technical Course Elearning solutions is the best Oracle Apps R12 technical course in Pune owned by well trained and certified trainers. The training is conducted by the best experienced IT professionals with skilled resources. The course structure is based on the real-time scenario so that it will…

₹25,000.00
Elearning solutions is the best SAP FICO training institute in Pune. SAP FICO is the Finance and Cost controlling module is one of the most important and widely used SAP ERP modules among organizations. As it is very robust and encounter almost all the business processes. In SAP FICO, FI…
Elearning solutions provide SAP SD training. The tutorials are designed for the students who desired to understand SAP SD concepts and implement them in practice. The SAP SD training is delivered by industry experts, who are aware of the real-time scenarios. Hence, supporting students understand, what will be there on…
SAP WM training is offered by Elearning solutions provides 100% hands-on practical classes. The primary focus of training is getting placement for all the students. The tutorials are designed for the students who wished to work on live projects for the organizations. The syllabus of SAP WM training is crafted…
Elearning solutions are the best SAP MM training institute in Pune. SAP MM (material management system) is one of the important models of the SAP ERP system, which is particularly designed for business processes. SAP MM deals with the entire material and inventory management of the organization. The module is…
Elearning Solutions best SAP ABAP training institute in Pune provides real-time training for students. SAP ABAP (Advanced Business Application Programming) is a programming language for building SAP applications such as SAP R/3 which runs in the SAP ABAP runtime environment. (SAP ABAP online course) SAP ABAP is used by organizations…







 WhatsApp us
WhatsApp us